Exhibit 1 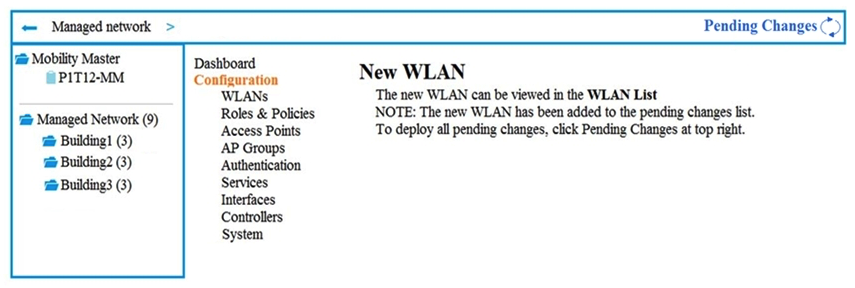 Exhibit 2
Exhibit 2 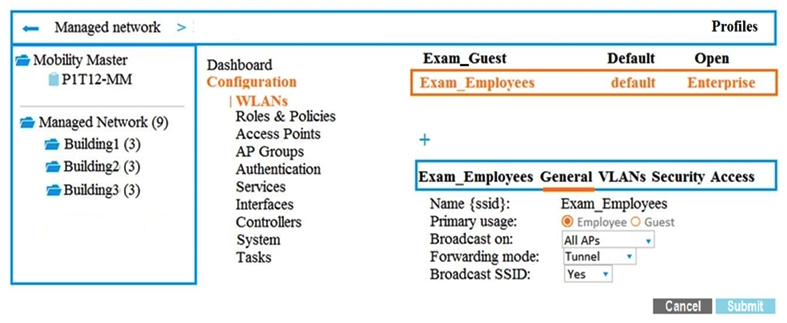 A company has an Aruba Mobility Master (MM) -based solution and needs a new WLAN for the corporate campus. A network administrator completes the creation of this WLAN, as shown in Exhibit 1. When administrators try to test a connection to the WLAN, the WLAN does not show up in the list of WLANs on the client. The administrator can see the WLAN in the list, as shown in Exhibit 2. What is the error?
A company has an Aruba Mobility Master (MM) -based solution and needs a new WLAN for the corporate campus. A network administrator completes the creation of this WLAN, as shown in Exhibit 1. When administrators try to test a connection to the WLAN, the WLAN does not show up in the list of WLANs on the client. The administrator can see the WLAN in the list, as shown in Exhibit 2. What is the error?
A) The configuration is not deployed.
B) The WLAN is configured at a lower level in the Managed Network hierarchy.
C) The Mobility Master (MM) does not have an active PEFNG license.
D) The WLAN is configured as a hidden SSID.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
A company has a Mobility Master (MM) -based solution. There is a hardware issue with the MM appliance, and, as result, all connectivity is lost between the appliance and the network. The network manager is concerned about how this will impact licensing. How will the Mobility Controller (MC) be affected?
A) The MC maintains its current licenses for 30 days.
B) The MC loses all licenses and cannot support APs or clients.
C) The MC contacts Aruba Activate and uses the licensing limits defined there.
D) The MC maintains only licenses that have been locally installed on it.
F) B) and D)
Correct Answer

verified
Correct Answer
verified